Features
Schedule and quality management by consulting-specialized staff. Detailed and clear guideline provision in consideration of clients’ characteristics.
Information system and security system hardening using tools reflecting various techniques and technologies
You can scroll horizontally.
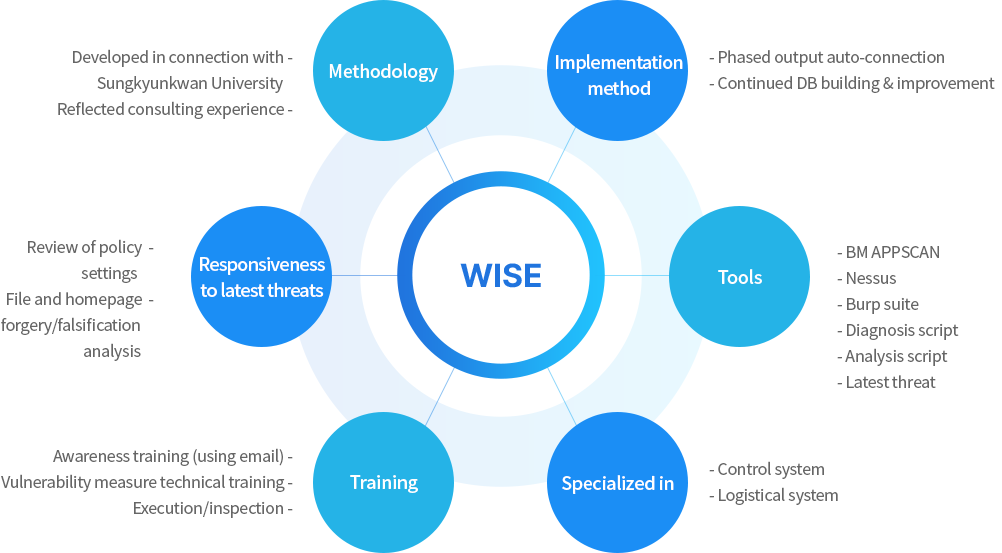
WISE (Wins Information Security Engineering methodology)
A practical methodology combining the necessary automated techniques and tools in the field of information system operation
Hardening Execution
Processed by a specific set of tools, systems, and experts for information security system hardening
in order to remove information system vulnerabilities and reinforce control
Information Security System Hardening
You can scroll horizontally.
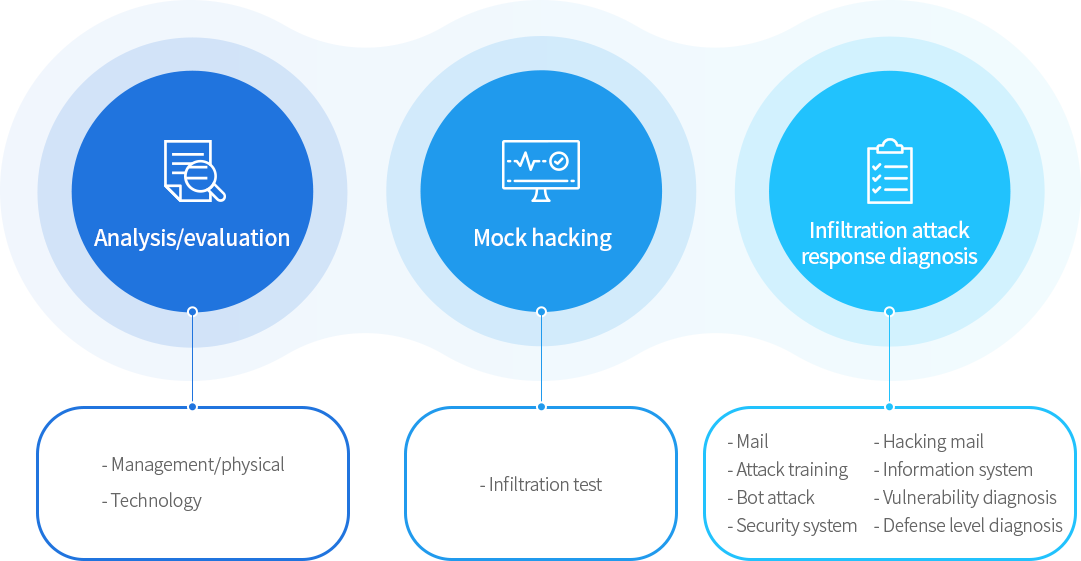
User Security Hardening
In order to reinforce user security in relation to recent issues and sociotechnological techniques,
utilize a hacking mail sending/analysis system and diagnose defense capability against malignant codes


Security Level Upgrade
Most vulnerable part of general security
Sociotechnological infiltration test on/offline-combined attack
- Education & training on hacking mail risk
- Response training upon hacking mail reception
- Safety diagnosis on latest hacking techniques
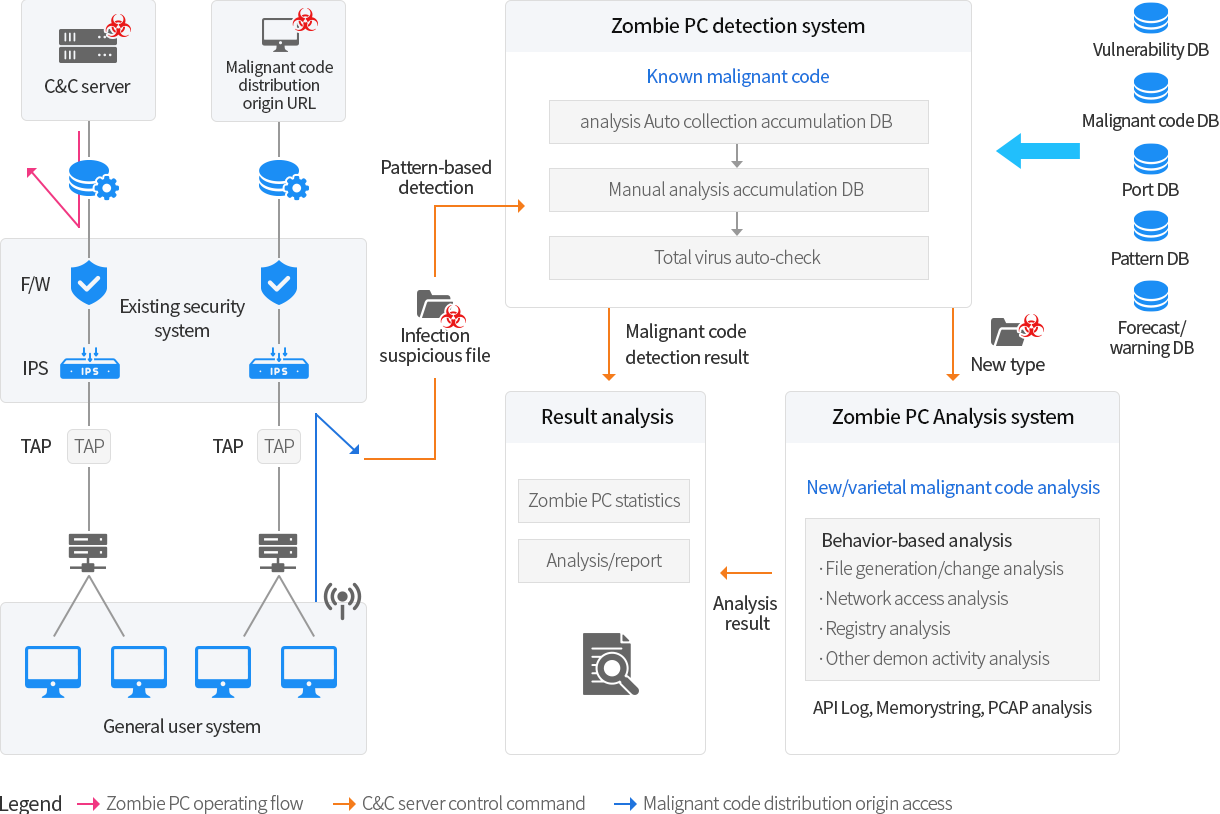
Information System hardening
Diagnose the defense capability against Bot attack and APT attack to information system such as server and PC
You can scroll horizontally.
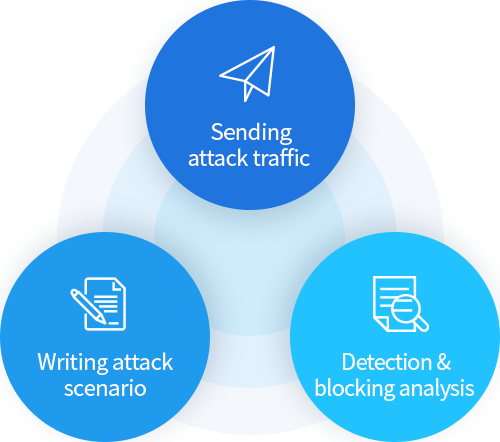
Security System Hardening
Diagnose the existing security systems established in line with company characteristics in terms of the defense level of detection and blocking by various security system in each phase using diverse attack traffic sending/analyzing systems.

Security Level Upgrade
Verify security system safety, which is easy to overestimate
