The multi-level security engine and context-aware engine mounted on SNIPER ONE-i detect and analyze in depth traffics flowing in real time to identify and block abnormal packets and sessions, ensuring network dimensional reliability and security.
SNIPER products that good to be with
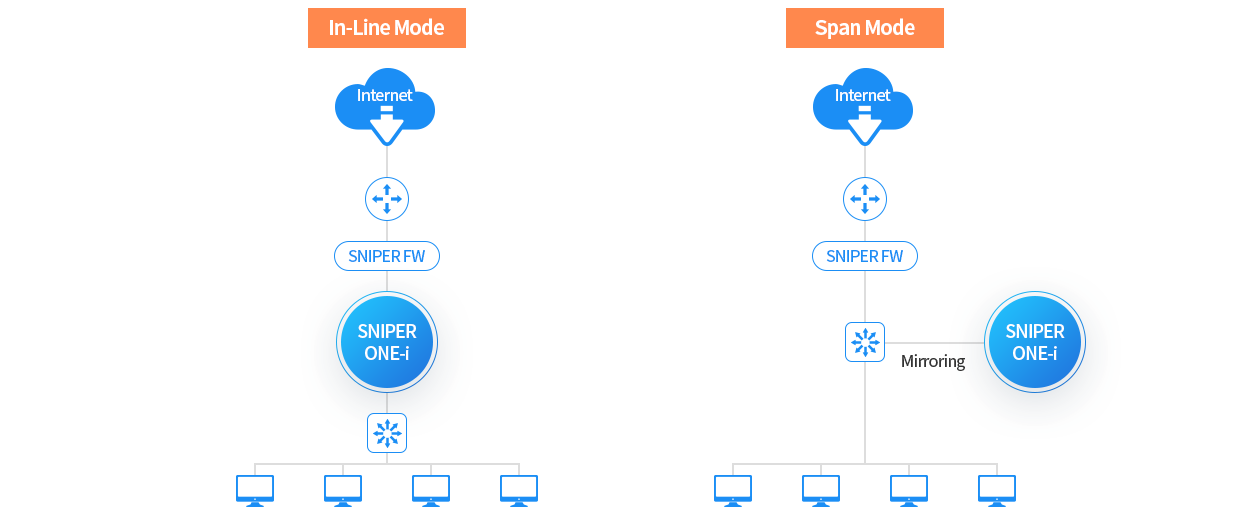
Product Outline / Description
SNIPER ONE-i is a new security solution to effectively respond to diversified communicating trends and new threats in the network. It implements in-depth analysis and correlation analysis techniques to examine network-based traffic threats and detects improper accesses or detects and cuts off external attacks.
SNIPER ONE-i, in order to defend users’ system and service from new threats for certain, has a dedicated module responding to more diverse attacks based on the existing SNIPER ONE-i, which can be introduced by selecting the necessary functions.
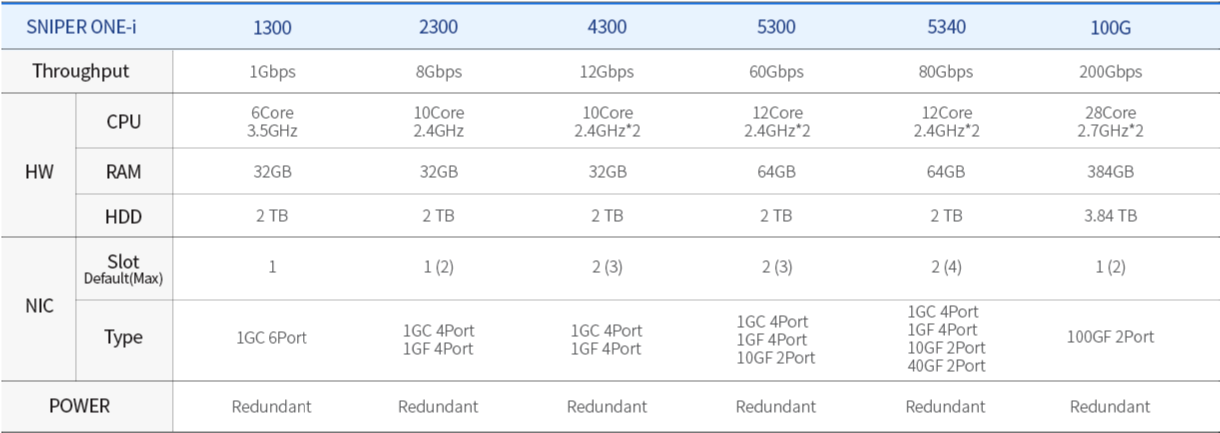
SNIPER ONE-i has the functions of Default IPS, HTTPS, RegEx, 3R(Aplication, Malware, User), and Reputation to perform intrusion response while providing other functions such as security control, user identification/authentication, audit of SNIPER ONE-i administrator’s activities, various statistical reporting, and updating.
Main Functions

IPS
- 24-hour real-time monitoring of any harmful network traffic
- IPv4 and IPv6 network traffic response (Dual Stack)
- IP Pool (Virtual IPS)-based network division and management
- Response to Zero-day attack with independent learning and customized signature writing
- Operable by executing multi independent windows for each function

HTTPS
- Private key registration for HTTPS session decryption
- Server-host network usage monitoring by SSL communication decryption
- Harmful traffic detection by SSL communication decryption

RegEx Response
- YARA-form signature regular expression response in addition to the Snort form
- Capable of detecting various attack patterns integratively with 1 policy using regular expression-type grammar

AR
- Continued update of in-service applications
- Performs permission, recognition, and control for application communication
- Sets IPs excepted from the application policy

UR
- Auto recognition of internal assets through session communication direction and port
- Identifying OS and browsers through signature and TCP structure
- Asset registration by user registration

MR
- Detection based on the signature and hash of files transferred via network
- Distinguish normal files from malware files through YARA engine and anti-virus
- Malware analysis and log recording by MDS hash value comparison
- Understanding 1-hour file download trend through event tracing function

Reputation
- Reputation policy setting by IP, state, URL through the definition of distributing agency or user
- Log recording under IP, state, URL-specific detection policy
- Time object setting to detect and block traffic inflow in a specific time period by policy

Virtual IPS
- Provides management functions for each area such as network division management by IP Pool function
- IP Pool/Segment based independent policy establishment and log/statistic management
- Monitoring and analysis are possible by dividing detection traffic/events by area
- Optimized detection for each zone by setting a selective detection license for each Virtual IPS Zone
Features
Diagram
Line-up