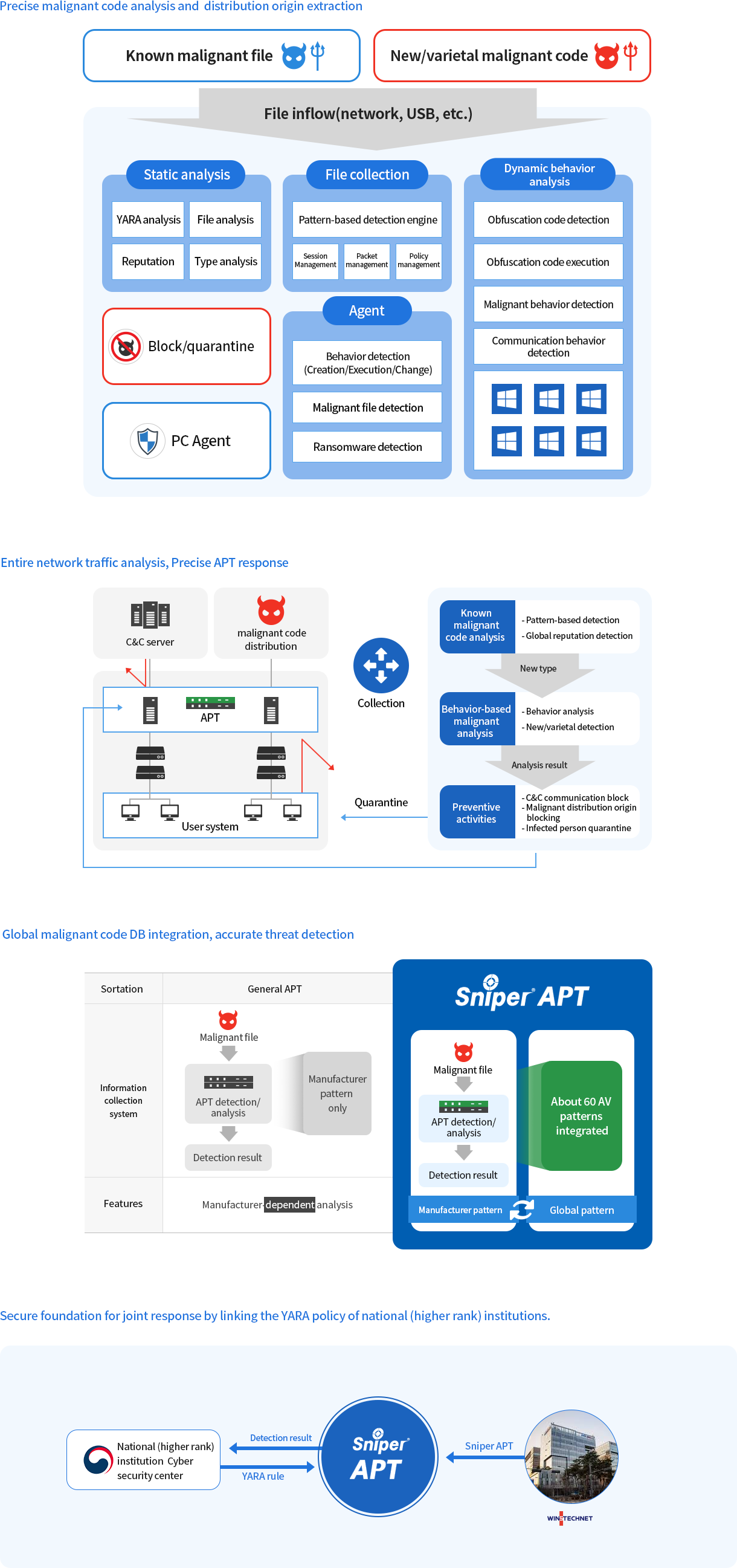
The sand box-based APT response system analyzes the whole network traffics to proactively detect and cut off latest threat attacks.
SNIPER products that good to be with
Product Outline / Description
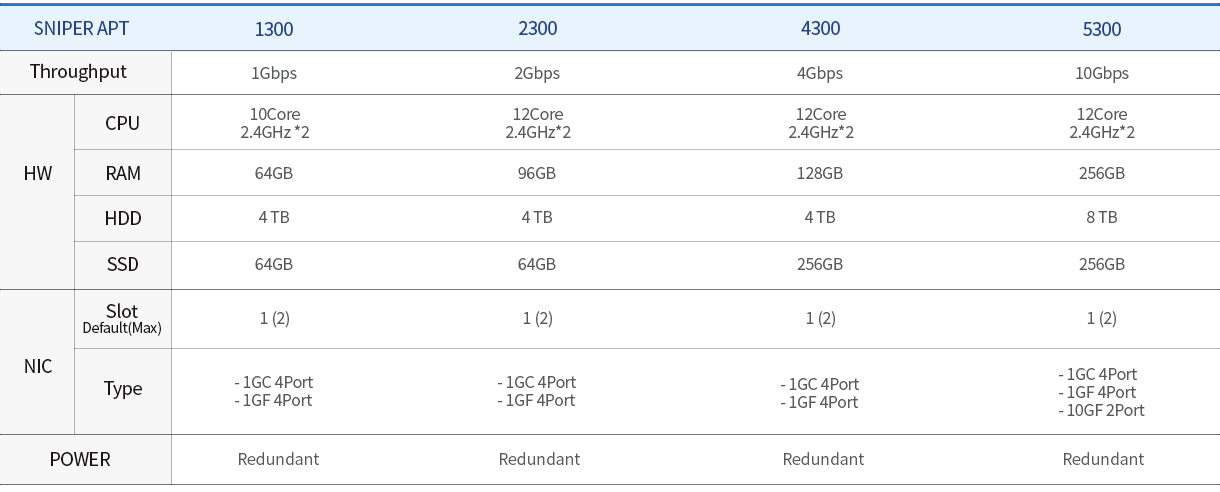
SNIPER APT is a full-range defense-in-depth system specialized in APT attacks. Its patented session-based multi-threading packet processing engine employed the high-performance packet processing technology of Korea’s No. 1 WINSTECHNET IPS (intrusion prevention system) and can collect files in real time in the unique manner of Sniper APT. YARA detection technology was applied to network security solution for the first time to detect and shut off malignant files.
SNIPER APT, based on Microsoft Interflow, SecureCAST connection with the world’s no. 1 anti-virus signature, comprehensively analyzes threats and can quarantine/block in real time with ransomware pattern and behavior analysis using PC Agent. The system also analyzes in depth document files (Hangul, MS Office, PDF, etc.) mainly utilized for APT attack using the behavior-based analysis and DANA(Document And Non-PE Analyzer) analysis engines.
The system presents every information at a look from network attack start to internal user infection with malignant codes, and response status.
The program employed technologies effective to find the trace of malignant code intrusion such as real-time malignant file and mail analysis record management, attack trend analysis by time, and malignity type distribution map.
Main Functions

Detection
- Real-time user download file extraction (URL, Mail, FTP, etc.)
- Whole user session collection and analysis
- Interlocking with SNIPER products and 3rd party products
- Detecting malware distribution sites and C&C in conjunction with CTI (Cyber Threat Intelligence

Management/Treatment
- Diverse statistics and search
- Integrated monitoring and policy setting
- Detailed statistical analysis report on malignant code
- Email quarantine and monitoring

Analysis
- Malignant code behavior-based (sandbox) analysis
- MS Office, Hangul, compressed file, etc. analysis
- Malignant code distribution origin and C&C server extraction
- Integrated analysis of domestic/global malignant code patterns

Cryptographic Communication
- Provide SSL encryption interface for safe central control by integration managers accessing remotely
- Provide SSL encrypted communication channel for safe control function execution in the Sniper APT Client

Agent (Infected PC Detection, Malignant Code Quarantine, Optional)
- Infected PC detection/malignant code quarantine
- Periodic detection policy update
- Auto/manual malignant code quarantine
- Support all Window systems (32/64bit)

Latest Vulnerability Response
- Operation of own WSEC (breach accident analysis response center) for vulnerable database building and continued update
- Builds the latest reputation database with continuous updates through CTI (Cyber Threat Intelligence) linkage
Features
Diagram
Line-up